Blog | Securence
Customize Securence’s Look For Your Company
Securence gives you the ability to customize your users’ interface, and reporting emails sent by the system (e.g. daily spam digest, stat reports). You can start your customization by editing your company settings through the interface and clicking on the “Upload New Logo” button near the bottom of the page.
The default Securence interface has a blue header with the Securence logo, and a white highlight on currently selected menu items and text. When you upload your own custom logo, and choose your custom colors, a “Powered By Securence” image will automatically appear on the page’s footer. The logo uploader only accepts PNG image files under a size of 1MB.
- Use a transparent background for your logo image file, this will allow seamless integration onto the header’s background.
- In the Securence interface, your logo will be resized to a maximum height of 50 pixels, while logos sent in system generated emails will be resized to a maximum height of 85 pixels.
- When Choosing a background color, your browser’s color picker will be displayed. In the picker, you can use the eyedropper tool to select any color visible on your monitor.
- The “Text & Accent” color will be used as the text color for the “Hi, [User’s Name]” text as well as the highlight color for the currently selected navigation item.
- Further customizations will be released in the future, stay tuned.
DKIM
DomainKeys Identified Mail (DKIM) has long been an internet standard, yet many administrators are still unfamiliar with what it is and how their organization can benefit from it. In this post we hope to clear up some of the confusion surrounding DKIM and what options are available as part of your email service with Securence.
What is DKIM?
At a basic level, DKIM provides a way for your outgoing email to be “digitally signed” by your domain. With this signature in place, a receiver can verify that your domain is truly the original source of the message. Additionally, since the signature is based on the actual message (headers and body), the receiver can also reliably confirm that the message has not been altered while in transit.
How does it work?
1. Hashing
First, the signing mail server generates a unique “hash value” for your message. It does this by feeding the message into a cryptographic hashing algorithm (usually SHA-256). This is a fancy way of reducing any message of any size down to a single, fixed length string of text that uniquely represents the contents of the message. Cryptographic hashing algorithms have the handy benefit of causing very similar text to produce vastly different hash values. For example:
"It was the best of times, it was the worst of times." SHA-256 hash: 38D141B35057BBB691B9756C20A6C31A0AB0BBF2076538A7FB6D9EE8835096D7 "It was the best of times, it was the worst of times," SHA-256 hash: 775FCE11D4FEC218D105CEC874901A5225B78C02EB6E86D8D4832464368C332A
Note that simply changing the period at the end of the sentence to a comma produced a completely different hash value. When the receiving mail server performs the same hashing algorithm on your message and gets the same result, it knows that the message is in the exact state it was in when originally hashed. Conversely, if a different hash value is produced on the receiving end, then some modification to the message has occurred.
2. Encryption
The calculated hash value is then encrypted using a private key owned by your domain. The public key counterpart is used to unlock or decrypt the hash for verification and is stored in your domain’s DNS record. In order to sign messages with Securence, you will generate this key pair in the admin portal. Securence stores the private key for signing while you make the public key available in a TXT record for verification.
3. Verification
When a receiving server sees a DKIM signature in the message headers, it attempts to decrypt the hash using the public key that is available via DNS. If the decryption succeeds, the server knows that it could only have been encrypted with the private key held in secret for your domain. It calculates its own hash value for the message. If it matches the decrypted one found in the signature, the receiver knows the message was not modified. The DKIM check is now complete.
What are the main benefits to signing with DKIM?
First, DKIM is an important part of protecting your domain from abuse. Email service providers can use the information gleaned from DKIM to identify and block fraud attempts.
DKIM signing can also improve delivery rates with email services that track sender reputation. For example, if Gmail is unable to authenticate a message using either SPF, DKIM, or DMARC, it is more likely that message could end up delayed or even marked as spam.
Additionally, DKIM is a necessary step towards implementing DMARC, which itself provides further protection from email scams and spoofing attempts. Though DKIM is not explicitly required for DMARC, implementing a reject policy in DMARC is strongly discouraged without first signing with DKIM. DMARC will be discussed in an upcoming blog post.
How do I setup DKIM in Securence?
Configuring Securence to sign your outbound messages with DKIM is a relatively straightforward process. Click here for a PDF which will walk you through the steps.
Summary
DKIM is an important and useful email authentication scheme. Using DKIM, your messages can be signed in such a way that receivers can trust they truly originated from your domain and have not been tampered with. DKIM signing is included with your Securence Outbound service. If you have questions about DKIM or any other part of your Securence email protection suite, reach out to us at support@securence.com.
CEO Fraud
Need to know
- CEO Fraud-type scams are increasingly prevalent.
- CEO Fraud Protection by Securence guards against sender name spoofing.
- In order to benefit, please configure the filter within the Securence admin portal.
“Good morning, Jim. Are you at your desk? I need you to do something for me.”
What is CEO Fraud
It begins with a quick morning email from a manager or CEO, which lowers the target’s guard. There are no suspicious attachments or links to raise alarm bells. This can even fool those who are otherwise adept at spotting a phish. If they respond, the scammer then asks for some kind of financial transaction to occur. (e.g. a wire transfer, gift card purchase, or direct deposit change)
Impersonation scams like this are continually on the rise. They are disturbingly easy to execute and can lead to dramatic payouts for the scammer. They also frequently pass through mail filters because they simply contain conversational text from previously unseen addresses. Also referred to as “whaling” or “spear phishing”, attacks like this cost organizations billions of dollars every year.
Standard domain name protection is ineffective
Standard email authentication schemes such as SPF, DKIM, and DMARC, which operate on the sender’s address, cannot protect against this since the scammer often does not spoof the address. They only need to spoof the executive’s name in order to achieve their goal. In fact, the message will frequently pass SPF, DKIM, and DMARC checks, since it may originate from a large ESP such as Gmail, Yahoo and Outlook.com. For example:
From: “Judy Smith” <ceo.12345@gmail.com>
Subject: Quick question
Hey, are you in the office today? I’ve got a favor to ask you.
The scammer is hoping for one of two things:
1. The target only sees the sender’s name, and assumes it is reliable.
2. The target sees the unusual email address, but assumes it was sent from the executive’s personal account, cell phone, tablet, etc. (The scammer may even include “Sent from my iPhone” at the bottom of the message to aid in this misdirection)
How can Securence help
CEO Fraud Protection by Securence guards the executive’s name, displayed as the sender, and is the key to the scam. If an email claims to be from a protected name in Securence, but the email address does not match, then Securence will take action. Standard actions include: block, quarantine, notify an administrator, or deliver the message after modifying it to include a warning.
Login to your account today to setup this critical feature. It is available under the Phish settings for your Domain, Group, and Company accounts. There you will also find further documentation, including best practices for configuration and tips on avoiding false positives during and after rollout.
As always, we welcome your feedback. Reach out to us at support@securence.com with any questions or concerns.
Zero Day Virus
What is it?
A zero-day virus is a computer virus that can either be a slight mutation of a previously seen virus or completely new. Therefore, the defining characteristic of a zero-day is simply that it is new. It has purposely been changed in order to be able to avoid detection from antivirus programs. They are designed to exploit your systems vulnerabilities and takes advantage of the fact that even the largest antivirus protection may have no current solution to defend against these mutated viruses. By attacking these vulnerabilities, the malware is able to sneak in and perform actions on your system that otherwise would not be permitted.
Most antivirus programs use signatures to search your computer for malicious programs and attachments. But a zero-day virus is good at hiding itself from being caught – It flies under the radar and does not send off a known signal. Antivirus software blocks against signatures that it has seen before. Each virus has a unique known signature, so when a zero-day virus changes it ever so slightly, it is able to slip through the cracks and send malicious content to you. While most programs develop a patch to fix the problem after the attack has occurred, that doesn’t protect against future vulnerabilities once the signature of the virus mutates yet again. Wouldn’t you want to stop the zero-day virus before it does any damage to your private and sensitive data?
How it attacks
One of the most common ways to infect a computer is to create a malicious email attachment. Most of the time, these attachments look completely legitimate. For example – say Fidelity Investments is your financial advisor. Most likely, you have their name, address, and personal advisor’s details in your contact list. If you were to receive an email that looked like this, would you open it?
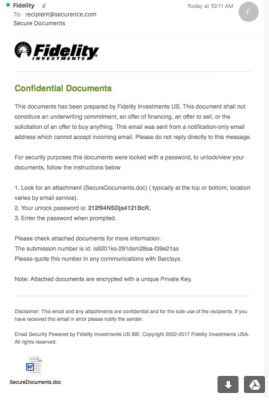
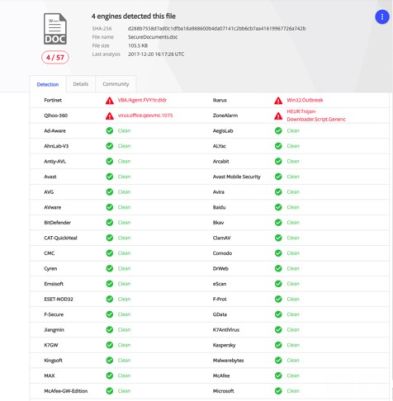
It’s from a trustworthy name, it’s on letterhead, and there are no spelling mistakes. Though this information looks familiar to you, it’s a trap. For example, we took this attachment at the time it was caught using Virus Total and out of 57 scanners (now there are 58), only four caught it.
It was able to fool Malwarebytes, MacAfee, AVG, and even Microsoft – and this zero-day virus was sent through Microsoft’s own Exchange servers!
By running this same file through Securence, the virus was caught. That is due to the fact that while many of the best antivirus software search for recurring signatures, Securence adds another layer of protection by using predictive blocking. Though we had never seen this specific virus, we are able to catch it because the virus used a pattern similar to what we had seen before.
Ensure you have the best protection
Of course, antivirus software is not without value. Some protection is better than none. However, zero-day viruses are specifically designed to circumvent the best names in antivirus, so for full protection, it is important to add extra layers where they are needed.
Instead of looking for just the “static” pattern that are typical for certain viruses, Securence looks for “fluid behavior patterns.” By looking for these flexible behavioral patterns for things that tend to exist but have never truly been seen before, we can predict how the virus may mutate in the future. This allows our program to be proactive and agile so we can stay ahead of hackers that want your personal information.
Why Securence
You, your company, and your clients deserve the best possible protection against zero-day viruses. Our solutions are affordable, complete, and incredibly agile. They also protect you from every angle including inbound and outbound email filtering, first-in-class encryption, secure email archiving, email shadowing, and more. Rather than providing retroactive fixes once a zero-day virus attacks, we focus our R&D on stopping the virus before your data is accessed. Only 7 percent of the top antivirus scanners caught this Fidelity virus the day it was released and Securence was one of them.
How To Get Even More Out Of Your Hosted Exchange
In any type of business, having some sort of email management program is a necessity. Not only do you want an email exchange that is reliable and easy to use, but you also want one that is secure. At the basic level, your exchange hosts your emails, contacts, and calenders. The thing that really sets one exchange cloud service apart from the others is the personalized support and email security for the enterprise and end users.
Simple migration is possible.

Migration is when you move your email mailbox from one exchange server to another (either
Nobody wants to deal with email fraud and security issues common with 365.
Email Fraud has become a critical threat to businesses of all types. Preventing threats such as spam, malware, and spoofing attacks is a requirement for

Customer service is key.
That’s the motto that every company should live by. Unfortunately, when dealing with bigger companies that sell exchange hosting services, that can easily get lost or is non-existent
Send US Internet an email today requesting a new exchange service and your account can be fully
CEO Fraud Protection by Securence
It’s common knowledge that email security is important in the business world. Hackers and spammers are relentless in their attempts to get their hands on your company’s sensitive information. A more serious threat is when they attempt to con you out of potentially millions of dollars. If the scam is a success, someone’s job will likely be in jeopardy. CEO Fraud is a real threat that can have damaging effects within a company or organization so it is important to be as prepared as possible to defend against it.
So what is CEO Fraud?

CEO Fraud, also called Whaling or Spear Phishing, is a type of email scam where the criminal impersonates an executive in the organization for the purposes of fooling another employee into initiating some kind of financial transaction (such as requesting a wire transfer or buying gift cards and sending the secret codes). Standard email authentication schemes such as SPF, DKIM, and DMARC, which operate on the sender’s address, do not provide protection against this since the scammer only needs to spoof the executive’s email address name in order to achieve their goal. In fact, a scammer’s email may actually pass SPF, DKIM, and DMARC since the message may originate from a large provider such as Gmail, Yahoo, or Hotmail.
In a busy work day, it would be easy to overlook a slight change to an email address. Here’s an example of a spoofed email a spammer may create:
Johndoe@company.com Johndoe@cornpany.com
An unsuspecting employee that receives a message from the latter email address likely won’t notice that the “m” in company is really a “r” and an “n” side by side. At a quick glance, it looks like an “m.” By making these slight variations in the fake email addresses, spammers can be successful at these whaling attempts.

But how do scammers know your company’s hierarchy, including emails?
It’s simple. They do their research. Then they know exactly who they need to impersonate, who to send the “fake” email to, when to send it, and what to say to make the email victim bite the hook. Scary, right?
Now you may be wondering – how is it possible to protect against this? CEO Fraud Protection by Securence guards the executive’s name that gets displayed as the sender and is the key to the scam. If an email claims to be from an executive as configured in Securence but the email address does not match, then Securence will take action. Standard actions include: block and quarantine, notify an administrator, or modify the message to include a warning.
CEO Fraud Protection gives you relief against whaling attacks. You shouldn’t have to worry that any email that you’re receiving could be an attempt to scam you out of money or information. With the customer in mind, Securence added this new CEO Fraud Protection feature in order to be able to protect both you and your company from as many threats as possible so you can focus on the things that really matter.
Benefits of Adding Email Continuity to Your Office 365 Account
Today’s business world runs on email, which is why having unencumbered, consistent access to your Office 365 account is absolutely essential. Without it, you could miss out on opportunities and lose important information. That is why many businesses are augmenting their Office 365 accounts with email continuity. This affordable service offers plenty of benefits for your business, and it will keep you in constant contact no matter what happens. We’ve put together a list of the major benefits of adding email continuity to your Office 365 account below.
But first, what is email continuity? Essentially, email continuity provides all users send and receive access to email during a power outage, internet routing failure or mail environment service unavailability. When outages occur, Securence Continuity automatically places new mail in the continuity folder for employee access. When the servers go back online, all information and emails that were received while it was out are transferred back to the original server, and everything continues on without any loss of data.
1. Never Lose an Email, or a Client
In a world where business is done via email and a lost one can mean the difference between a sale or not, having your email continuity gives you peace of mind—the peace of mind that you won’t lose an email when servers go down without your knowledge, and the peace of mind that your correspondence will be saved and accessible once those servers are back online.
2. Stay in Constant Contact
When email goes down, business can grind to a halt and that is lost time, money, and opportunity. But email continuity (https://www.securence.com/how-to-prevent-business-interruptions-by-using-email-continuity/) lets you still send and receive emails and important attachments no matter what happens. This keeps you in constant contact with your clients and employees and ensures every email gets to where it needs to be.
Email continuity services are an essential aspect of running a business in an email-driven world. When a missing email can mean the difference between a sale or no sale, any loss of data or service can be detrimental, which is why so many businesses are turning to Securence for email continuity services. Rather than rely on a single server that’s outside your control, get a proven service that ensures you will never be out of touch with your clients, letting you conduct your business from anywhere and still have every email you need. Contact Securence today to learn more about our email continuity services for Office 365.
Benefits of Adding Outbound Filtering to Your Office 365 Account
In today’s business world, a missed email can mean the difference between landing a big client and losing out on an opportunity. That is why so many businesses are adding additional security to their Office 365 accounts, including outbound email filtering services.
Outbound email filtering helps keep your emails more secure and helps ensure that they get delivered to their recipients. Without it, you can end up without important correspondences, and that means you can even lose out on business. Here are just a few of the benefits that businesses are enjoying by adding outbound email filtering to their Office 365 accounts.
1. Stop Ending Up in the Spam Folder
While most email clients are getting better and better at sorting spam from actual correspondence, they still are not perfect. They can still read some emails that do not comply with certain standards as spam, which means your emails can end up ignored in someone’s spam folder. This can be extremely detrimental in some instances where important or time-sensitive information is being transferred, so it’s imperative that your emails end up where they need to be.
2. Stay Compliant with Security Standards
For many companies that work in the tech sector and beyond, security compliance is mandatory when looking for and working with other companies and businesses. If your company does not meet their required security protocols, you simply will not get the contract. That is why so many businesses opt to add enhanced security to their Office 365 services. Office 365 as-is often does not meet the stringent security protocols and requirements of other businesses, so it pays to upgrade those services with additional features, including outbound email filtering.
3. Avoid Spam Issues
Has anyone ever hacked your email and then sent emails to everyone in your contact list? This is a common practice with hackers to this day, not just because it’s simple to do, but also because it can actually be quite effective for spreading malware or getting people to give up their personal information. And when it comes from you, even when you did everything in your power to stop it, it looks bad. Outbound email filtering (https://www.securence.com/how-an-email-filtering-service-help-secure-your-businesses-future/) can help catch suspicious email activity, including mass emails that are sent from your account, and stop them before they end up in the inboxes of important clients, family members, or friends. So even if you do end up compromised, it can stay contained to your account.
Email filtering is an essential aspect of modern business. Without the right security protocols, you could end up losing out on important business and having important messages end up in the spam folders of your clients. But with additional security features for your Office 365 account, including outbound email filtering, you can enjoy added security and more effective emailing. If you are in need of extra email security for your business, contact Securence today. With a variety of email security options available at affordable prices, we can make your emailing more effective and secure without biting into your budget.
Benefits of Adding Email Encryption to Your Office 365 Account
Email encryption is no longer an added bonus in the business world. It is an expectation and often a requirement, which is why every business needs to consider additional email security, especially when using Office 365. If your business uses Office 365, then you can benefit from the added security and safety of email encryption, here are just a few reasons why.
1. Compliance
Security in the modern business world is a top priority. There are expectations for all companies to adhere to minimum security protocols and, unfortunately, standard Office 365 is generally insufficient. If you are a small business or any business that is looking to expand, there is a strong chance that you will be audited for security protocols before you can do business with some companies. One of these security expectations will include email protocols, and email encryption will be expected.
Much of the reason for this is the new ways email hackers will access your information. In many instances, you can inadvertently download malware that doesn’t just try and shut down your computer, but which instead archives your correspondences. This can lead to issues of important information being sold online, including access to bank accounts and other sensitive information. Without proper encryption, this information can go somewhere you, and your clients, do not want it to go.
2. Privacy
Your business is just that: yours. No one has the right to access your private information and correspondences without your permission or without going through the proper legal channels. Email encryption (https://www.securence.com/what-is-encrypted-email/) gives you an added layer of privacy that Office 365 does not offer. This not only means that your business is yours, but it also means that your privacy will remain a top priority.
3. Client Confidence
Security is one of the most sought-after aspects of all businesses today. Companies and clients alike expect their collaborators to keep communications and information safe and secure. Breaches are no longer something that is acceptable. In fact, they can often lead to the end of professional and profitable relationships, which is why so many companies need to use email encryption to protect their correspondences.
While Office 365 is a powerful email tool, its security protocols are often lacking, considering the many ways in which hackers and malicious email scammers infiltrate email accounts. Today, the phishing schemes can be quite complex, so much so that even the most astute people can fall victim. But with email encryption, you can protect yourself from these attacks because of the additional security.
4. Added Trust
When you use email encryption, your emails can go on a safer list for those receiving, meaning there’s less of a chance of your emails being blocked or heading straight to the spam folder. And since so many companies use different security protocols, having that added layer of trust can mean you can communicate with your business partners more readily.
If you are using Office 365 as your email client, then you will need to consider additional security protocols, including email encryption. Securence’s email encryption services are affordable and easy to use, requiring no additional software or training.
US Internet Hosted POP/IMAP & Exchange Email Hosting
You have choices when it comes to your email security solutions, but far too many people over-look the importance of email security spam filtering – which is actually the most important part of your hosted email solution. Today we present an overview of POP/IMAP so you can see why email security is so critically important. As a leader in email filtering security, we are happy to provide advice on this and other e-security topics.
Many people do not understand that email choices boil down to more than just service provid-ers. The types of services, their advantages and disadvantages, and their cost is also very im-portant, especially as spam and email scams become more sophisticated. But what are these different kinds of email options, and how can they help you?
In general, email types fall into three categories: POP, IMAP, and exchange email hosting. Gen-erally, the first two can be combined into something more effective as well, but it is important to have security protocols on both inbound and outbound emails, no matter the type, to keep your information safe. Here is each one in a little more detail.
1. POP
POP (post office protocol) is probably the simplest email type and one that has remained popu-lar for a very long time. The reason it remains such a widespread option comes down to that simplicity, and the fact that every single email service provider can work with POP.
The downside to POP comes down to usability and security. In general, it only works well with a single device and has very limited use on mobile devices, especially smartphones and tablets. Receiving email is also easier, while sending emails can pose a problem when outside a trusted wireless connection. And since the system is so simple, it necessitates additional security proto-cols to ensure the data that is exchanged remains safe.
2. IMAP
Internet Message Access Protocol (IMAP) is steadily rising in popularity because it is perfect for people with email accounts that need to be synchronized between multiple devices. And since almost everyone in the business world needs both a computer and smartphone, IMAP makes perfect sense. IMAP also makes email migration easy, often just taking a few clicks and a pass-word or two. This email type is also perfect for business because it saves sent mail from any device, not just a desktop or laptop.
One of the drawbacks for IMAP is space. Since everything is stored on a server, email accounts can fill that server quite quickly. As emails become smaller and more efficient and servers be-come larger, this issue has lessened significantly in the past few years.
Another drawback to the proliferation of devices is that there are more opportunities for at-tacks, which is why additional security measures are often taken with IMAP email.
Most of the time, POP and IMAP are combined for a more effective email delivery system that is easy to sync, easy to use, and that can send and receive emails across multiple devices, all while ensuring every device is synchronizing in near-real time.
3. Exchange Email Hosting
Designed specifically for businesses, exchange emails hosting is meant for companies that need a professional email system, one that works across all devices and platforms. Unlike IMAP, which traditionally only syncs messages, exchange email hosting can sync contacts, calendars, emails and more across all modern devices, from tablets to desktops to phones. Migrating is simple, too, and it increases accountability because all sent and received emails are being saved, no matter the device. Sometimes exchange email hosting interacts strangely with non-professional platforms, like Outlook, but these rare instances are generally easy to fix.
The Securence Solution
There is a right email system for your business that depends on how you do business, with whom you do business, and on what your specific needs will be. Working with an experienced security and email company will help you develop the right email system to keep your business on the path to success. Securence provides industry-leading email security tools for your US hosted POP or exchange hosting service. No matter your company’s email protocols, using ded-icated, experienced security experts is a must. We will ensure that your inbound and outbound emails are safe and that the data that is enclosed is protected. Our high level of security, unlim-ited storage, and easy access to efficient phone support rival other industry solutions. Experi-ence our difference today.



